In today’s digital landscape, where mobile applications have become an integral part of our daily lives, ensuring their security is paramount. Android, being the most widely used mobile operating system, is a prime target for attackers. This is where Android application penetration testing comes into play. It’s a proactive approach to identify and mitigate vulnerabilities before they’re exploited by malicious actors. Let’s dive into the depths of Android app penetration testing to understand its significance and how it’s conducted.
Pre-Requisite for Setup
For Windows
- Emulator (Genymotion / Nox / Android Studio )
- ADB ( Android Debug Bridge )
- Python
- Frida ( pip install frida-tools )
- Frida Server for Android
- Objection ( pip install objection )
- Burpsuite
- Frida Script : RootDetectionBypass
- Frida Script : SSLPinningBypass
For Linux
- Emulator (Genymotion / Nox / Android Studio )
- ADB ( apt install adb -y )
- Python ( sudo apt install python3 -y )
- Frida ( pip install frida-tools )
- Frida Server for Android
- Objection ( pip install objection )
- Burpsuite
- Frida Script : RootDetectionBypass
- Frida Script : SSLPinningBypass
Let’s Setup Genymotion
- Once Genymotion is installed, open Genymotion and click on + icon on the top right corner.

- Now it will open a new window, where you can select the device model you want to install.

- After selecting the Android Device, we need to configure which android version we want it to be.
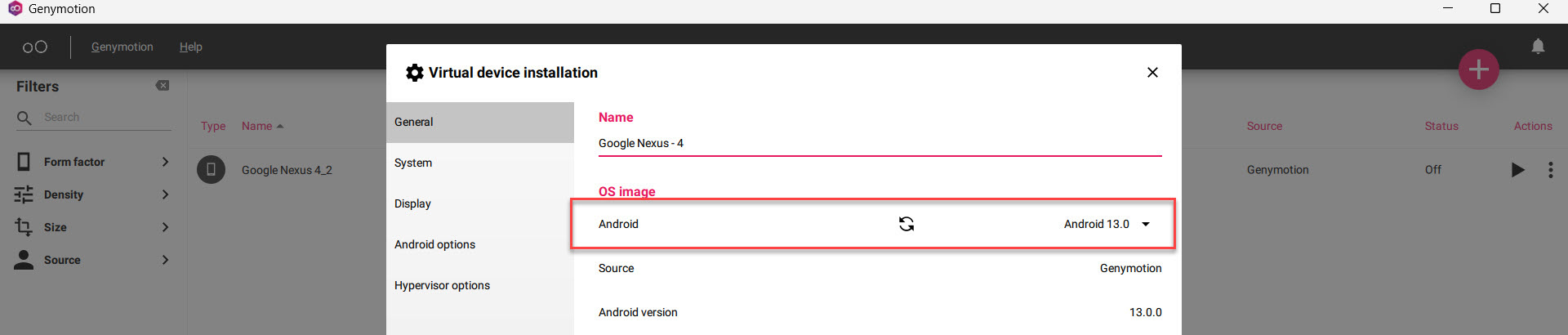
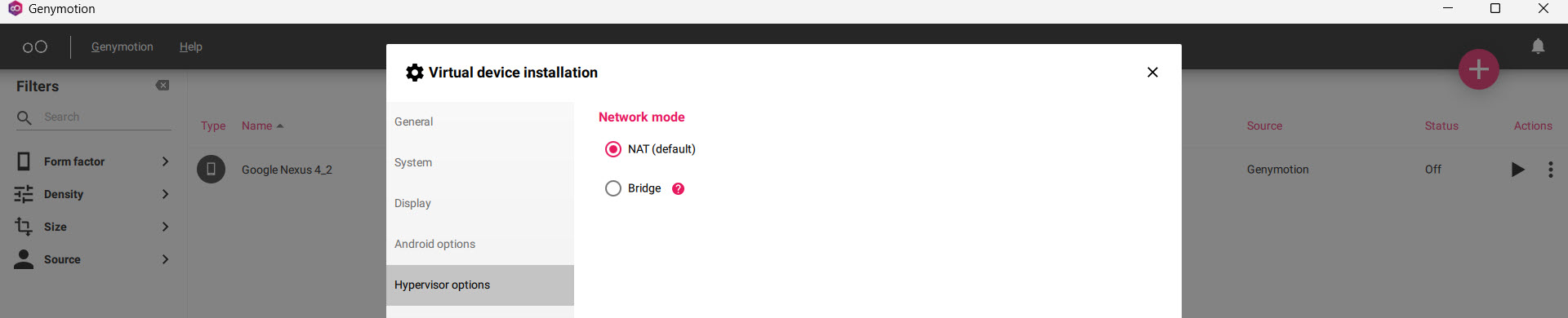
- I am going to install “Android-10” for the setup. After this just click on Next and always select “NAT” for Network Mode and click on Install.
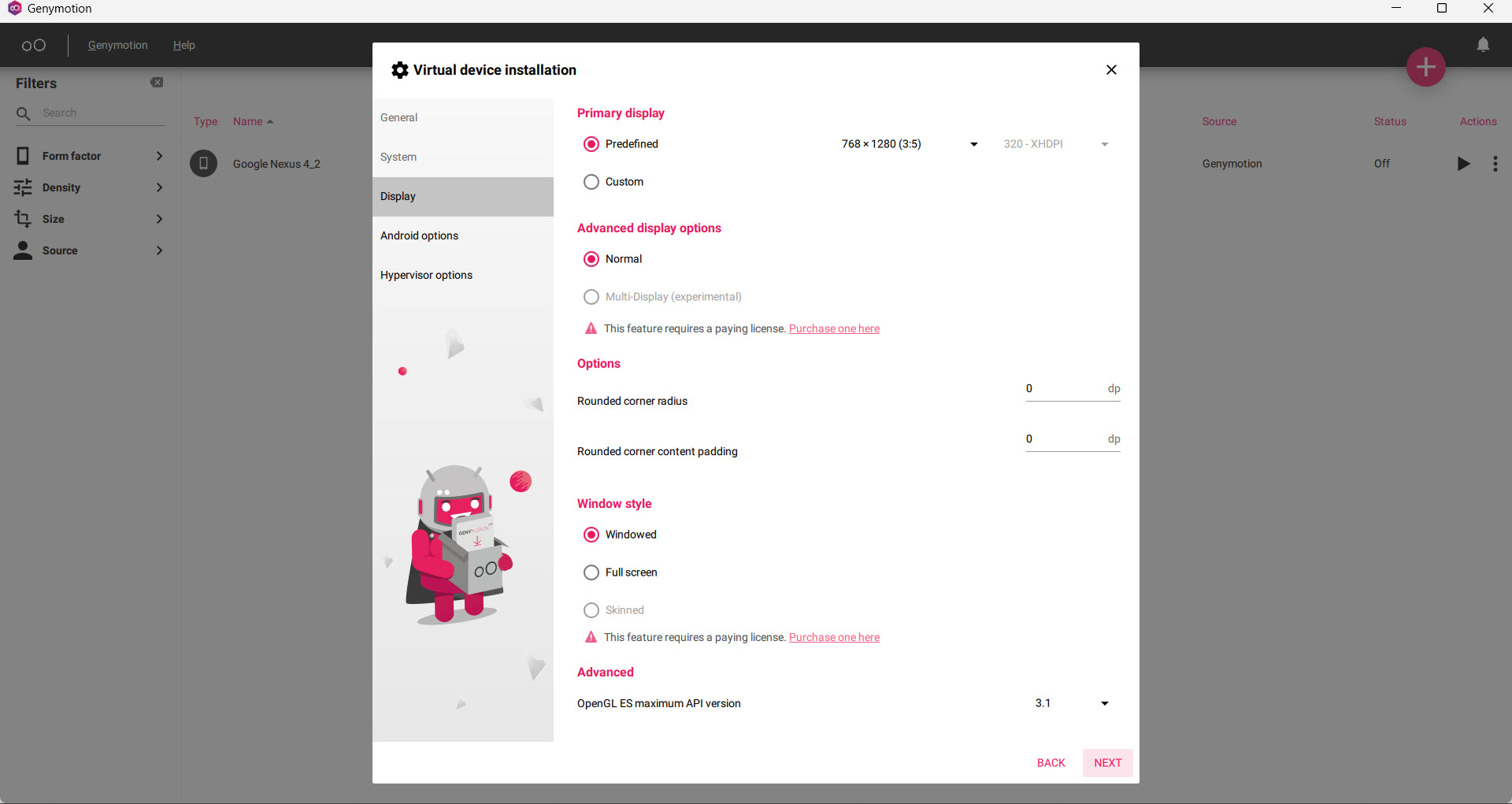
- Now, it will take sometime to install, once install we will get a notification on the top right corner to start the device.
- Let’s start and setup our android device.
Lets Setup Burpsuite with Android Device
- Open Burp Suite & click Settings to open the Settings dialog.
- Go to Tools > Proxy.
- In Proxy Listeners, click Add.
- In the Binding tab, set Bind to port 8080 (or another port that is not in use).
- Select All Interfaces and click OK.
Discover more from Upcoming Hackers
Subscribe to get the latest posts sent to your email.