The Common Vulnerability Scoring System (CVSS) is a standardized framework used to assess and communicate the severity and risk of security vulnerabilities in software, hardware, and firmware. CVSS provides a numerical score reflecting the severity of a vulnerability, which helps organizations prioritize their response and remediation efforts.
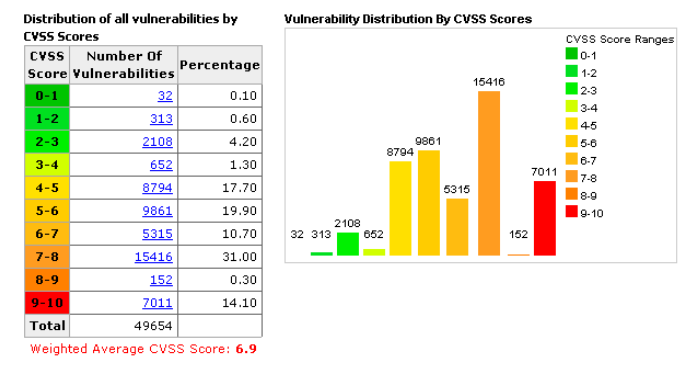
CVSS consists of three metric groups: –
1. Base Metrics:- Reflect the intrinsic characteristics of a vulnerability that are constant over time and user environments. Base metrics are typically the most critical metrics and include factors like:
- Attack Vector (AV):- How the vulnerability can be exploited (e.g., network, adjacent network, local, physical).
- Attack Complexity (AC):- The conditions beyond the attacker’s control that must be met to exploit a vulnerability.
- Privileges Required (PR):- The level of privileges an attacker must possess before successfully exploiting the vulnerability.
- User Interaction (UI):- Whether or not a user needs to be involved for an exploit to be successful.
- Scope (S):- Whether the exploit affects other components apart from the vulnerable component.
- Confidentiality, Integrity, and Availability Impact (C, I, A): The impact on the system’s confidentiality, integrity, and availability if successfully exploited.
2. Temporal Metrics:- Reflect the characteristics of a vulnerability that may change over time, such as:
- Exploit Code Maturity (E):- The current state of exploit techniques or code availability.
- Remediation Level (RL):- The level of remediation available (e.g., official fix, temporary fix).
- Report Confidence (RC):- The degree of confidence in the existence of the vulnerability and the credibility of the known details.
3. Environmental Metrics:- Reflect the characteristics of a vulnerability that are unique to a user’s environment, including:
- Collateral Damage Potential (CDP):- The potential for loss due to the exploitation of the vulnerability.
- Target Distribution (TD):- The proportion of systems that are likely to be affected.
- Confidentiality, Integrity, and Availability Requirements (CR, IR, AR): Measures how important maintaining these security properties is for a given system/application.
We can use the CVSS calculator to generate our CVSS score –
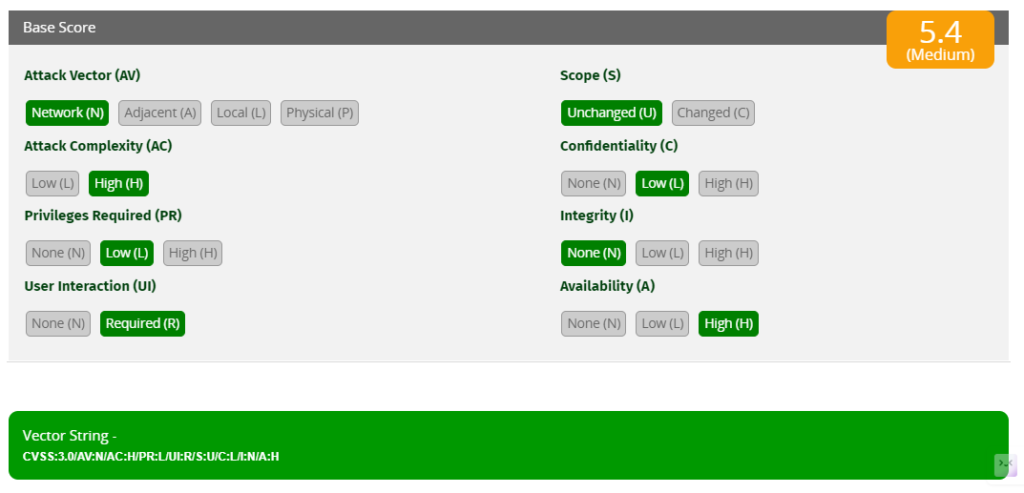
The CVSS score ranges from 0 to 10, with higher scores indicating more severe vulnerabilities. The framework is widely used to help organizations prioritize their response to vulnerabilities by understanding their potential impact.
Discover more from Upcoming Hackers
Subscribe to get the latest posts sent to your email.