The Open Web Application Security Project (OWASP) is renowned for its emphasis on web application security, but it also offers valuable insights and guidance on a range of other security issues, including firmware security. Among its resources is the OWASP Firmware Security Testing Methodology, which is detailed below:
Common Firmware Vulnerabilities
- Sensitive Information in config files
- Hardcoded Secrets like passwords, API Keys, Private Certificates.
- Backdoors with CVE
- Insecure Functions
- Insecure Network Services
- Runtime Vulnerabilities during code execution
- Insecure Data Transfer
- Insecure Web interface
- Common firmware vulnerabilities include:
- Unpatched Vulnerabilities
- Insecure Boot Mechanisms
- Inadequate Encryption
- Hardcoded Credentials
- Buffer Overflows
- Improper Input Validation
- Insecure Update Mechanisms
- Insufficient Access Controls
- Default or Weak Passwords
- Insecure Communication Protocols
- Lack of Proper Error Handling
- Firmware Backdoors
- Insecure Firmware Storage
- Inadequate Logging and Monitoring
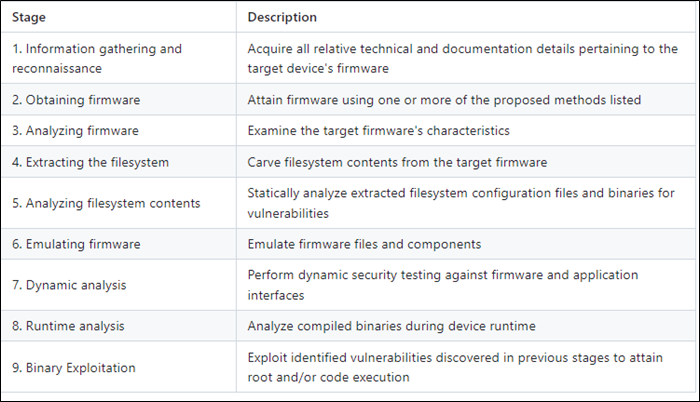
Firmware testing Methodology
- OWASP Firmware Testing
- IOT Security verification Standard
Firmware Compliance Standards
- NIST 800-53
- Rev-3
- Rev-5