In the previous document, we completed the installation and checked and captured some traffic. In this document, we will explore how the Burp Suite tool works and examine all its important features.
We will explore these features –
- Target
- Proxy
- Intruder
- Repeater
Note:- Here we learn about Burp Suite Community, which is the free version. There is also a paid version called Burp Suite Professional. In the free version, we get fewer features compared to the paid version. The Community version offers basic features for manual testing but lacks many advanced tools and automation features available in the Professional version.
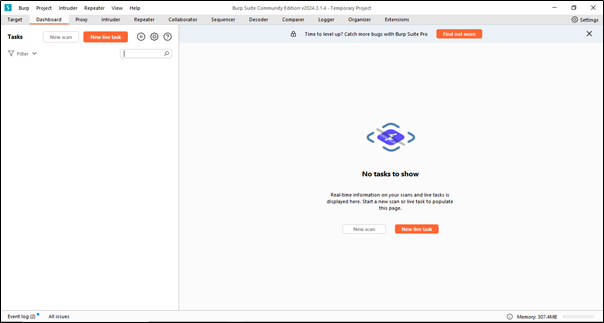
When we open Burp Suite, we will see the first window, which is called the Dashboard.
Now, we will understand each feature one by one-
- Target:- The Target tab in Burp Suite is used for defining and managing the scope of your web application security testing.
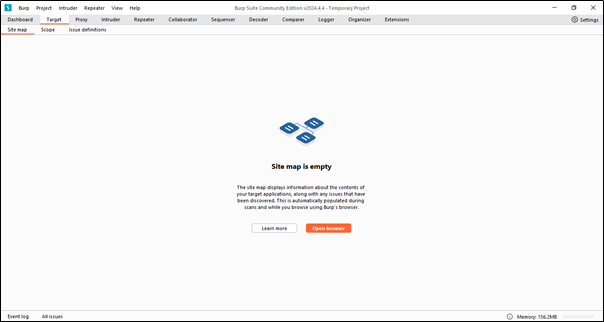
When we click on the Target tab, we will see this interface.
Whatever activity we have done in the browser, it captures that. Let’s check if it has captured it or not.
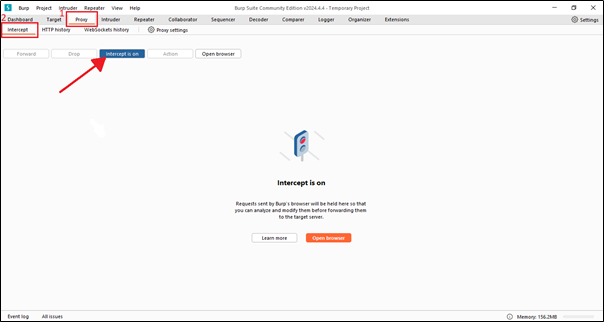
First, we need to turn on the intercept. In the installation part, we already explained why we use intercept.
Now, just go to Firefox and search for a website or anything else.
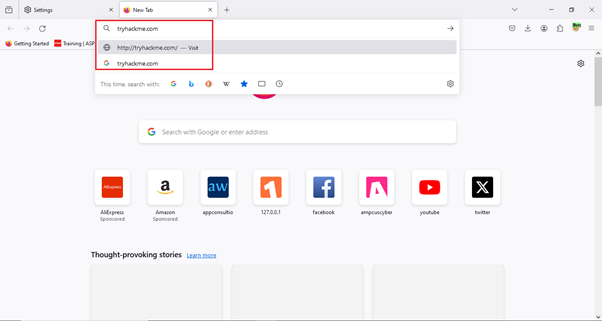
We will type the TryHackMe website to see if it captures this or not.
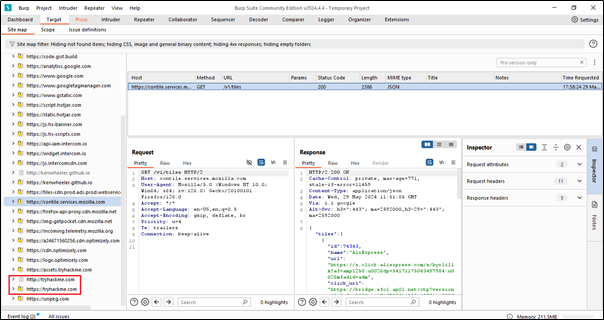
We can see at the bottom that what we just searched in Firefox is being shown.
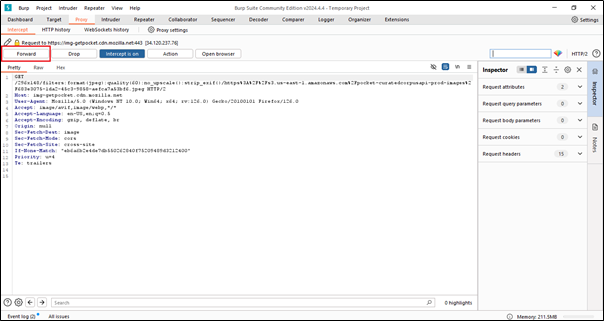
If it doesn’t show up here, just do one thing: go to the Proxy tab and click on the Forward button. It will definitely show up.
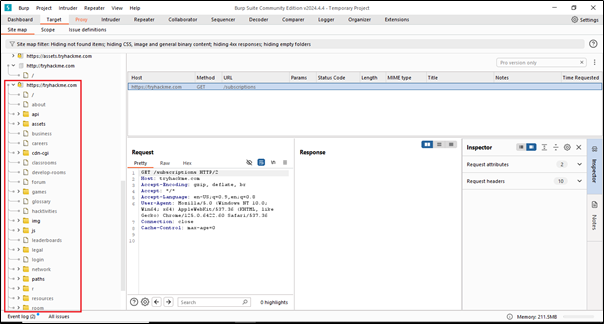
In the Target tab, you can see three options: Site Map, Scope, and Issue Definition. Let’s understand these options. We already know the first option, so let’s understand the remaining two tabs.
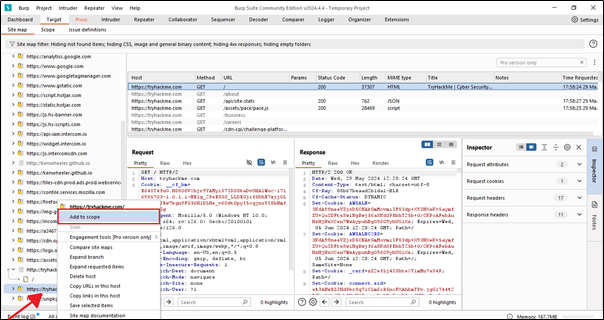
We use scope to target specific websites. For example, if I want to target a website like TryHackMe and send a request to this particular website, we have two options. The first option is using the scope feature, and the second option is using the Site Map, where we can achieve the same result.
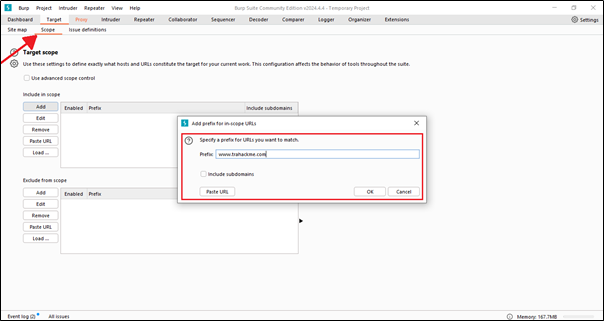
This is the 1st option.
Just click on ‘Yes’
Now our targeted website or url added on the scope.
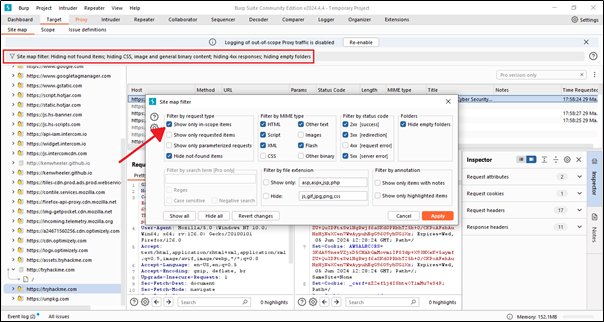
Here, we can also filter the scope. If we click on ‘Show only in-scope items,’ it will display only our targeted scope.
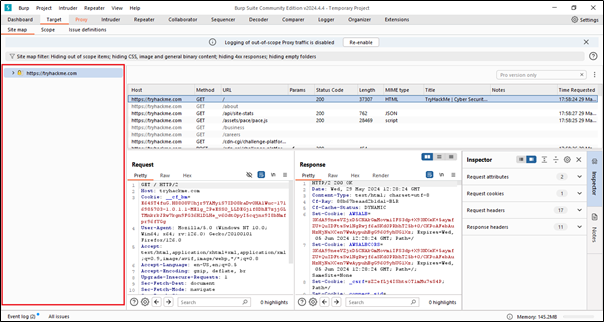
We can see that only our targeted scope or URL is shown, and all other URLs are hidden.
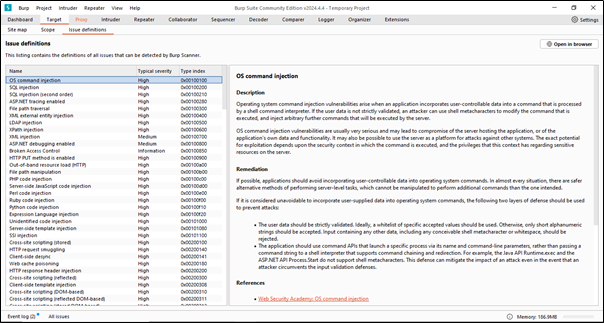
The Issue Definition tab in Burp Suite is used for managing and customizing the way Burp Suite identifies and reports security issues during a web application security assessment. This tab allows users to define the types of issues Burp Suite should look for and provides detailed information about these issues, including their severity and impact.
2. Proxy:- The Proxy tab in Burp Suite is one of the most fundamental and powerful components. It allows you to intercept, inspect, and modify HTTP and HTTPS traffic between your browser and the target web application.
So lets understand the each feature of Proxy –
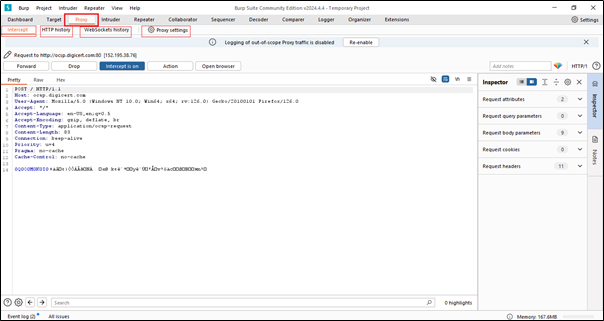
When you click on the Proxy tab, you will see four options. The first is Intercept, the second is HTTP history, the third is WebSockets history, and the last one is Proxy Settings.
We’ll understand each of them.
Lets 1st understand the intercept.
The Intercept tab in Burp Suite provides powerful capabilities for manually controlling and manipulating HTTP/S traffic during web application security testing.
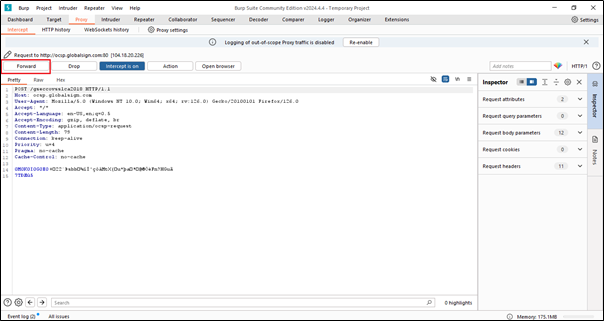
The “Forward” button in the Intercept tab of Burp Suite’s Proxy module is used to forward intercepted requests to the target server. When interception is enabled, Burp Suite captures HTTP/S requests and holds them in the Intercept tab until you decide whether to forward or drop them.
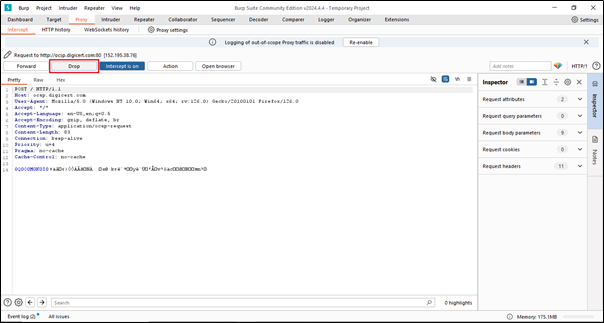
By using the “Drop” button in the Intercept tab of Burp Suite, you can selectively discard intercepted requests.
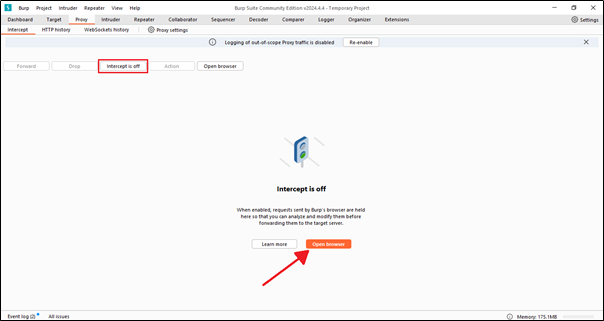
When interception is enabled, Burp Suite captures HTTP/S requests and holds them in the Intercept tab until you decide whether to forward or drop them.
Additionally, we can open a browser directly from here; there’s no need to go to Mozilla Firefox. Just click on the ‘Open Browser’ button.
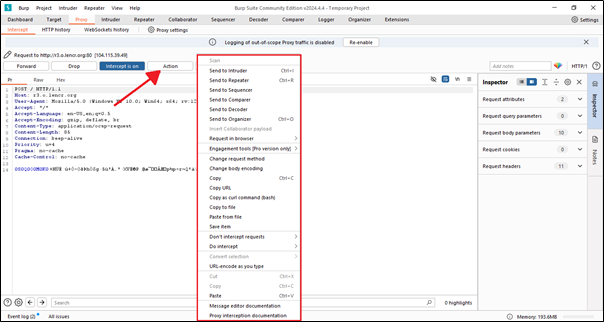
The Action button in Burp Suite is used to perform various operations on the items listed in different tabs. It provides a range of options for managing, analyzing, and manipulating HTTP/S requests and responses during web application security testing.
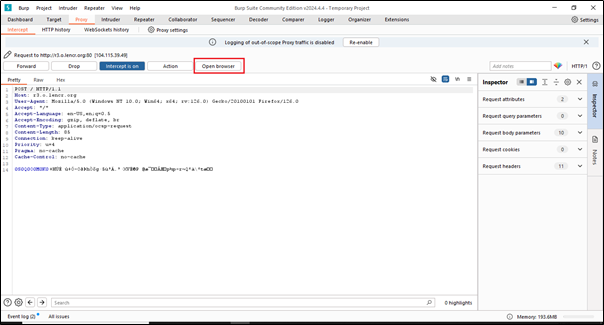
As previously discussed, we can open the browser from the Intercept tab. Additionally, we can use the “Open Browser” button to do the same thing. To do this, simply click on the button, and it will directly redirect to the browser.
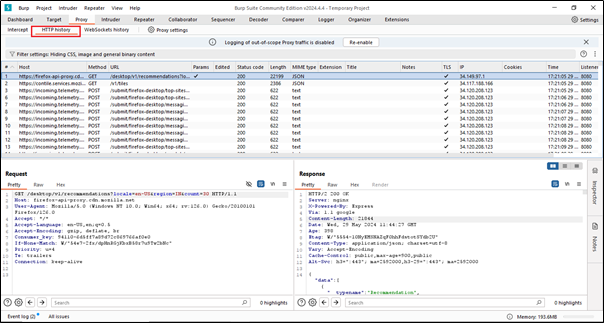
Whatever activity we have done in the browser, or in technical terms, the traffic, can be seen in the HTTP history.
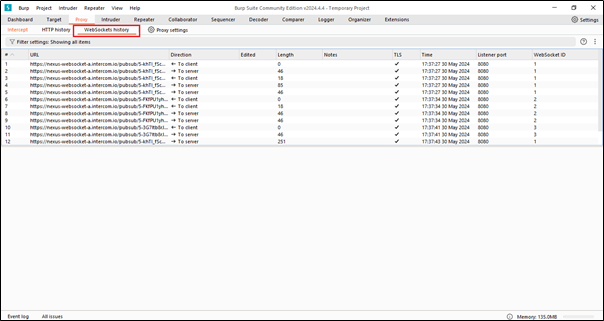
The WebSocket History feature in Burp Suite is used to capture and analyze WebSocket messages exchanged between the client and the server during communication.
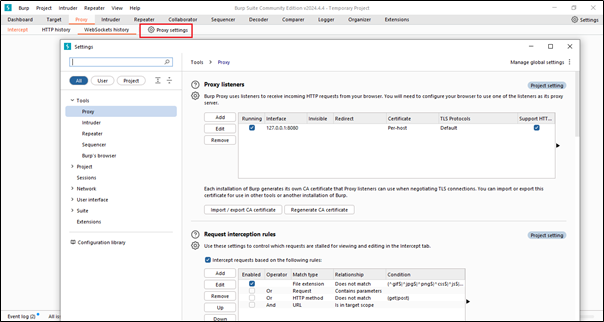
Here we can see all the proxy settings related to every tools and project.
So lets understand the Proxy –
Let’s just log in to a random account and see if the username and password we entered are captured or not. In simple terms, we can call this a brute force technique.
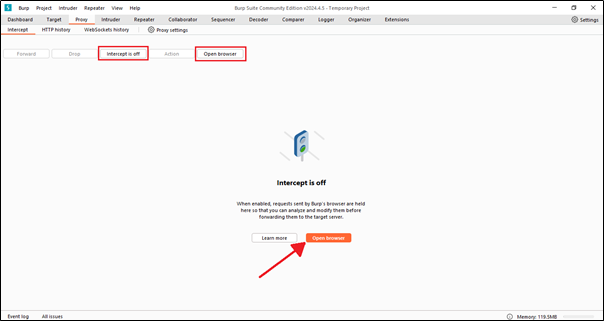
Now, first on the intercept and just click on the ‘Open Browser‘ button. It will redirect you directly to the browser.
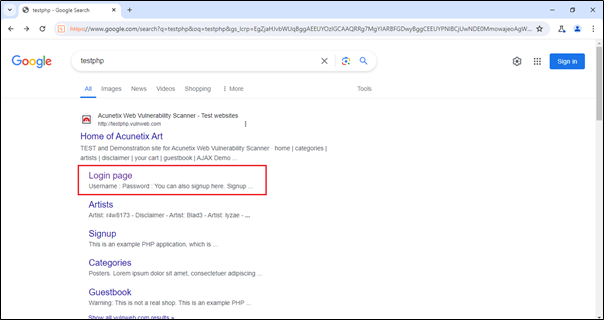
Just click on the ‘Login Page’.
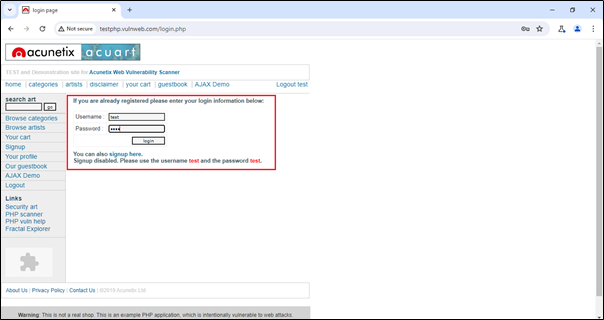
We are just adding a dummy username and password to see what happens in Burp. It will capture it or not?
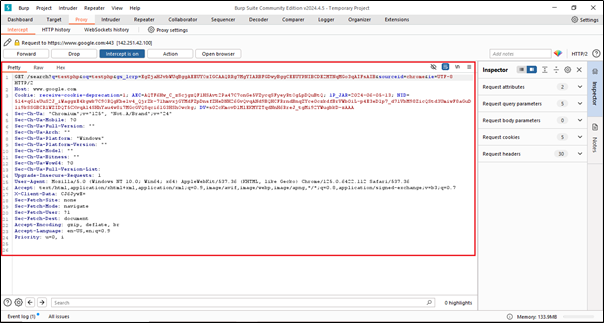
We can see that we have received this data after entering the URL in the browser. However, we can also see our dummy username and password in this data. To verify, we need to click on the forward button. This will definitely show the dummy username and password. In the login form, we have added the username ‘test’ and the password ‘test’.
3. Intruder:- Intruder is a powerful tool within Burp Suite, a popular web application security testing software. Burp Suite is widely used by security professionals and ethical hackers to identify vulnerabilities in web applications. The Intruder tool specifically is designed to automate customized attacks against web applications.
To use the Intruder, we need to follow some steps. First, we have to open a browser to begin testing –
In order to automate customized attacks against web applications, we need to send our responses or traffic to Intruder.
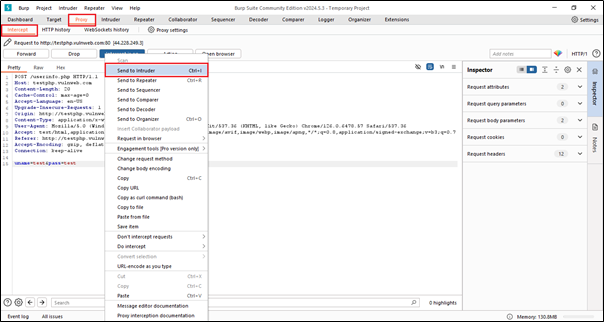
After sending to Intruder, we need to go to the Repeater tab manually.
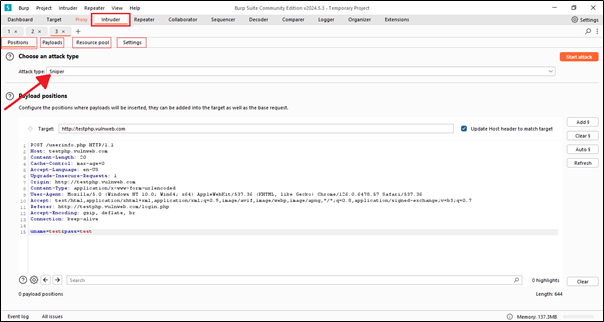
This is the Intruder tab. Inside the Intruder tab, we can see four new tabs: Positions, Payloads, Resource Pool, and Settings. We’ll understand each option in detail –
Inside the Intruder tab, the first is the Positions tab. In the Positions tab, we can see the attack type, payload options, and target URL.
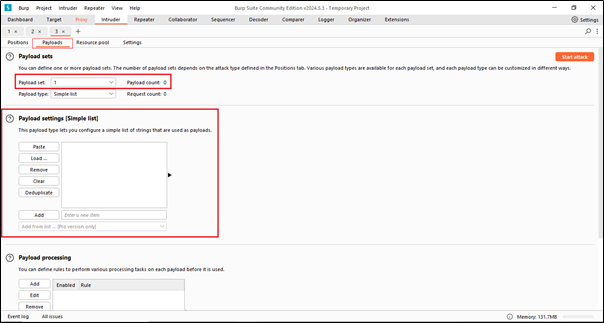
This is the second sub-tab of Intruder, called Payloads. In this tab, we can set the payloads and specify the payload type. Additionally, we can see the payload settings where we can add, delete, load, clear, and deduplicate payloads. These operations can be performed here, and we can also start the attack directly from this tab.
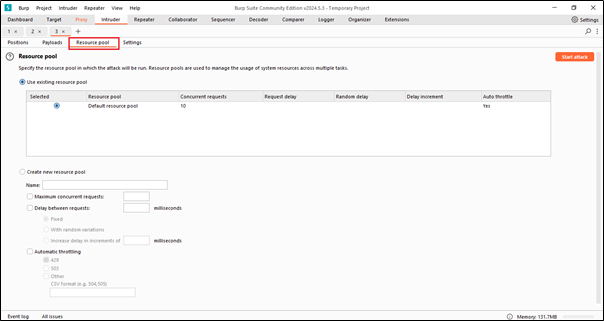
The Resource Pool tab within Intruder is used to manage and allocate resources for your automated attacks.
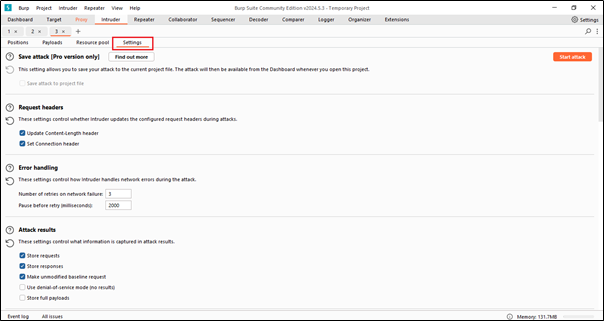
Using these settings tabs, we can manage or change all the required settings of Intruder.
4. Repeater:- is a tool within the Burp Suite web security testing suite. It allows users to manually craft, modify, and resend individual HTTP and WebSocket requests to observe the responses from the server.
In Intruder, we send the request from the proxy to Intruder, just as we send the request to Repeater.
Conclusion:- Burp Suite is a comprehensive and powerful web vulnerability scanner and security testing tool widely used by cybersecurity professionals. It offers an array of features for identifying, analyzing, and exploiting web application vulnerabilities, including automated scanning, manual testing tools, and advanced functionality for customizing attacks. Its integration with other security tools and extensibility through a robust API make it a versatile asset for enhancing web application security. Overall, Burp Suite is essential for ensuring the robustness and security of web applications.