What is Macros?
Macros in Burp Suite are automated sequences of HTTP requests that you can configure and replay within the tool. These are particularly useful for handling complex workflows, such as those involving multiple steps for authentication, session handling, or accessing certain parts of an application.
Why Use Macros in Burp Suite?
Automating Repetitive Tasks:- Macros can automate repetitive sequences of actions that would otherwise need to be performed manually, saving time and effort.
Session Management:- They help manage sessions by automating the process of refreshing session tokens or cookies, ensuring that your session remains active during long testing periods.
Complex Authentication:- For applications with multi-step authentication processes, macros can automate these steps, making it easier to maintain an authenticated state.
State Preservation:- They ensure that the application remains in the correct state for testing, such as maintaining certain conditions or preconditions required for specific tests.
Let’s walk through a real-time example where macros can be particularly useful: handling automatic re-authentication in a web application.
Scenario
You are performing a security assessment on a web application that requires user authentication. The session token expires every 10 minutes, and the application requires re-authentication by submitting the login form again to obtain a new session token. Re-authenticating manually during a long testing session is time-consuming and disruptive, especially when using tools like Burp Intruder or Scanner that may run for an extended period.
Let’s Implement the Macro –
To perform this task, we will use the PortSwigger 2FA bypass using a brute-force attack lab.
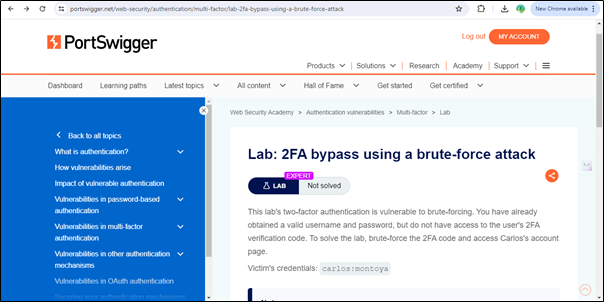
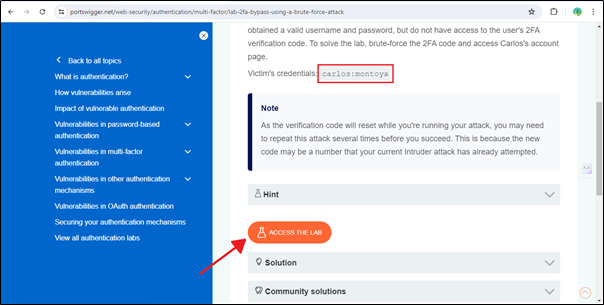
Just copy the victim’s credentials that we will use in this lab and click on ‘Access The Lab’.
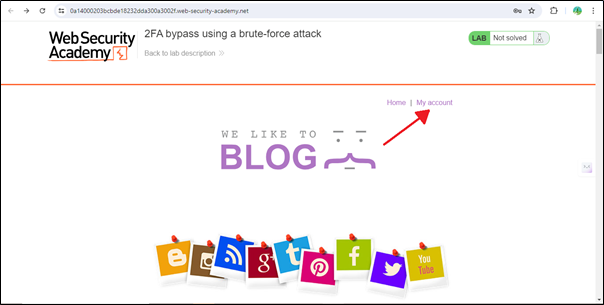
Just click on the ‘My Account’ page, and it will redirect you to the Login Page.
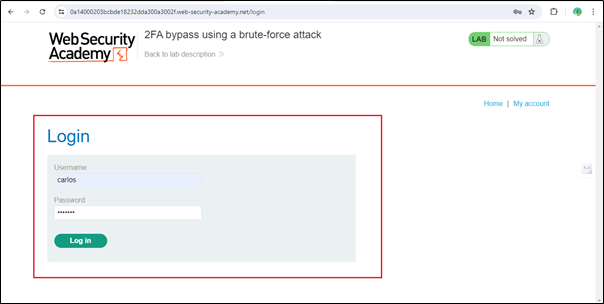
So we have to enter the victim’s username and password that we copied previously.
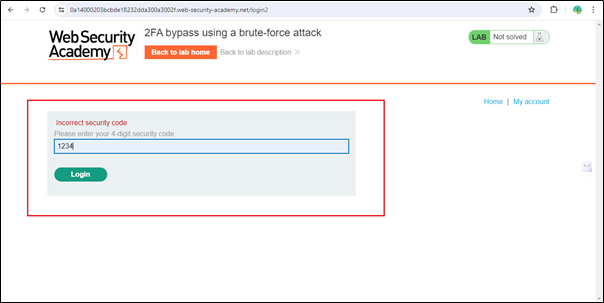
Now we have entered a wrong OTP. If we enter the wrong OTP twice here, it will automatically redirect to the login page again with an ‘Incorrect security code’ message.
So, when it goes back to the login page, it will generate a new CSRF token. Then we have to enter the username and password again and also enter the OTP. We can’t perform the brute force method here because it will only return a 200 HTTP code twice before failing, so to avoid this kind of situation, we use macros.
So let’s see how we can use that?
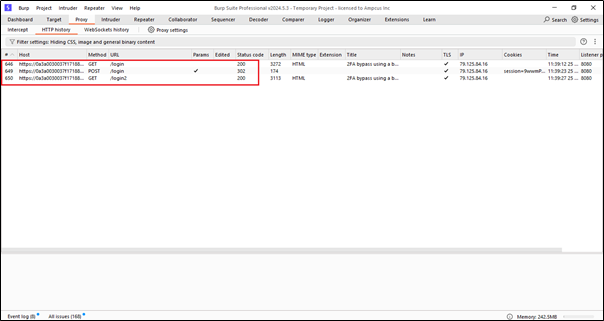
Here we have three requests: two GET requests and one POST request. In the POST request, we have entered the username and password data, so we will automate these 3 request in the background.
So, in order to automate this process, we need the Burp Suite Professional version. We then have to go to the Proxy -> Proxy settings -> sessions.
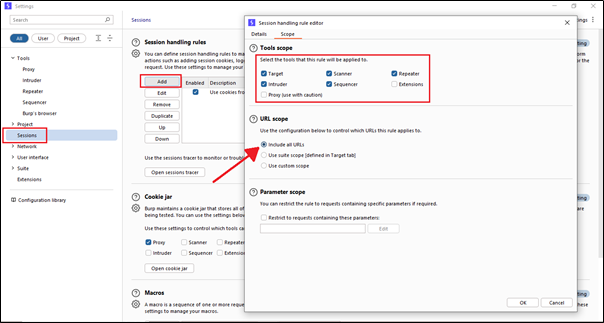
In Burp Suite, in the Session tab, there is a session handling rule. Just click on ‘Add‘ and you will see two options: ‘Details‘ and ‘Scope.’ Click on the ‘Scope‘ option. In the ‘Scope‘ option, there is a URL section. Just click on the ‘Include all URLs‘ option. Using this option, all URLs that come in the background will be included.
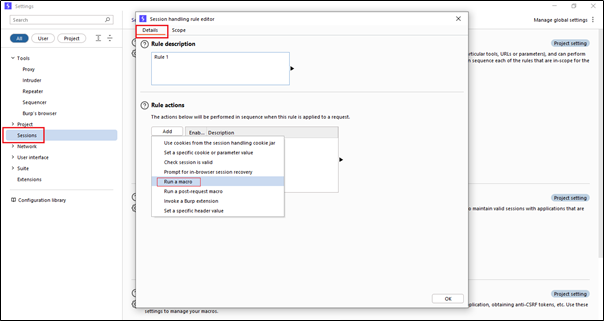
In the Session tab, inside the Details section, we can see the Rule Actions. When we click on ‘Run a macro,’ we simply have to create a rule that runs a macro.
And after clicking on the Run a macro option it will redirected to the next window where we have to select the macro.
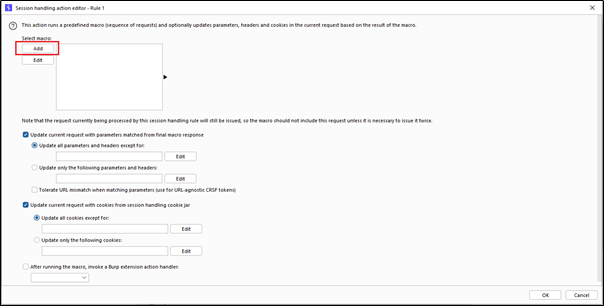
Just click on the ‘Add‘ option, and it will redirect to a new window where we have to select the macro for automation.
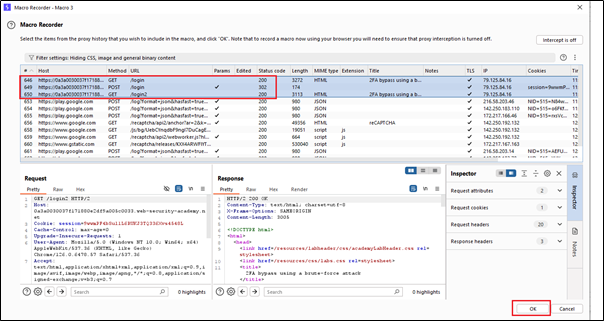
We have selected only the pages we want to automate. There are three requests and three steps: first, the login page; second, we log in; and third, the login is completed. Essentially, we want these requests to be repeated automatically in the background. This will generate a new CSRF token each time, allowing us to perform brute force attacks.
When you click the ‘OK‘ button, a new window will appear where you can test your selected macro.
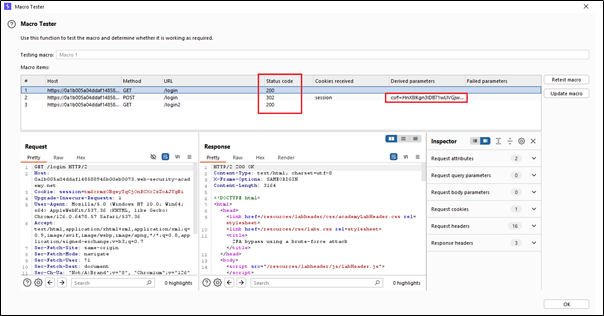
Here we can test our macro and see that it is generating a new CSRF token each time we test it.
Now it’s time to perform the brute force attack using the Intruder tab.
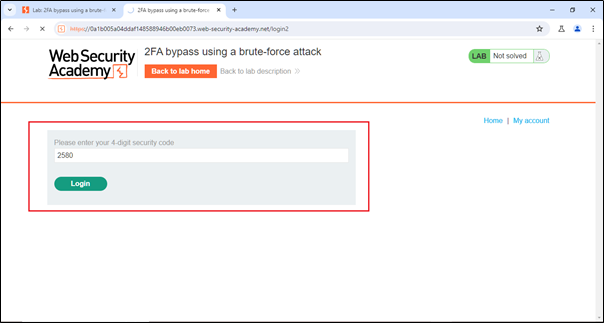
Now we will intercept this request in Burp Suite.
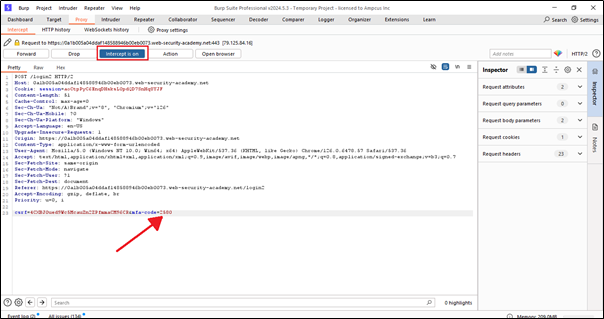
Now I want to perform a brute force attack on the OTP to try possible combinations for login.
To send this request to the Intruder, simply right-click on the tab and select ‘Send to Intruder
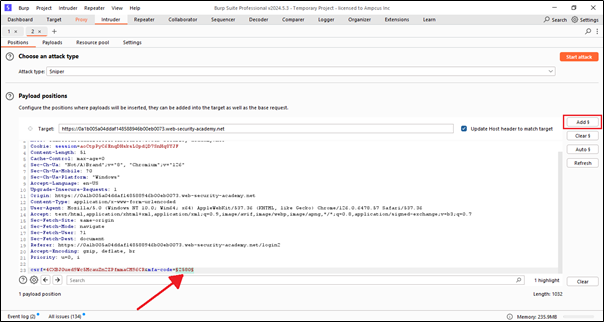
In the Intruder tab, there is a sub-tab called ‘Positions’ where we can see the request that we recently sent from the proxy. Now, we need to add the MFA position, which is at 2580. After that, we can proceed to the next sub-tab, which is ‘Payloads’.
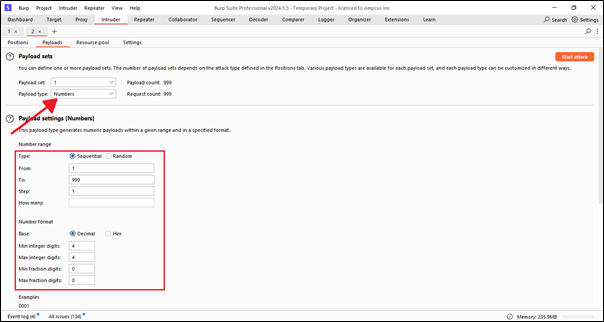
Here in the payloads option, for the brute force, we need to choose the type. I have chosen ‘Numbers’ because I want to brute-force the OTP. Next, in the payload settings, we can specify the number range. For example, it can start from 1 and go up to 999, trying all combinations. Another option is the number format, such as minimum integer, maximum integer, and others.
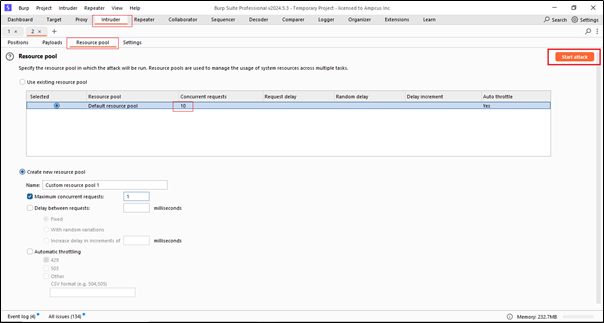
Basically, the resource pool is a kind of thread that specifies how many requests will be sent at a time. Here, we can see the concurrent requests set to 10, which means it will send 10 requests at a time, now just click on the start attack button.
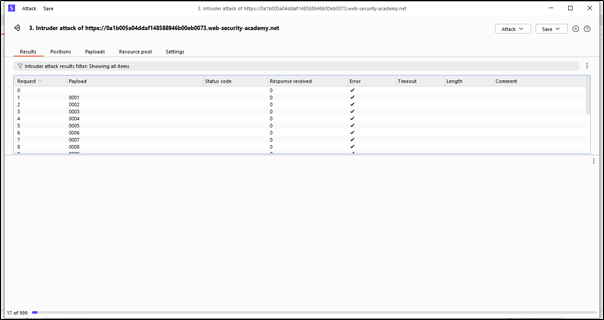
We can see that the brute force attack has started, and it will try all possible combinations to crack the OTP.
Now we can see our request in the open session tracer. To do this, go to Proxy -> Proxy settings -> Session -> Open session tracer.
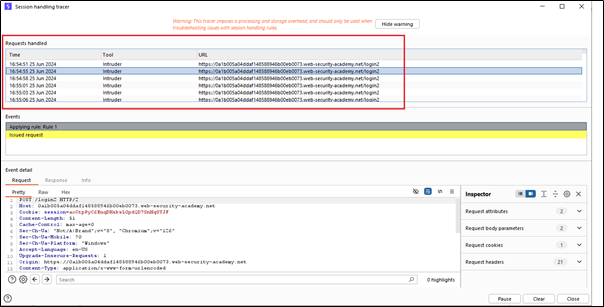
Here, with each request, a new CSRF token is generated. This is how we can perform macros in Burp Suite.