Defense in Depth is a comprehensive cybersecurity strategy that employs multiple layers of defense mechanisms to protect information systems and data. The idea is that if one layer of defense is compromised, the other layers will continue to provide protection. This multi-layered approach enhances security by creating redundancy and making it more challenging for attackers to breach systems. Here are the key components of Defense in Depth:
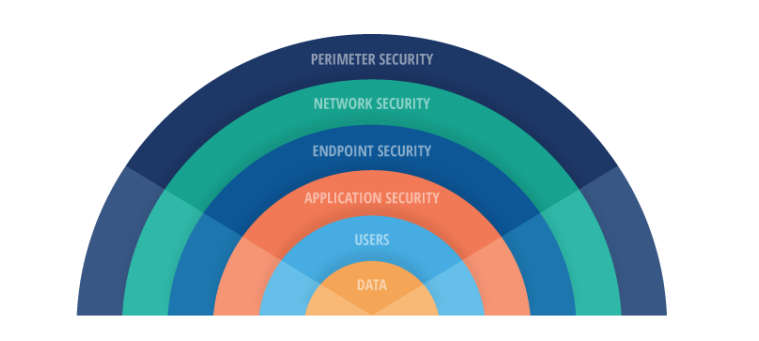
Perimeter Security
- Firewalls: Control and monitor traffic entering and leaving the network.
- Intrusion Detection and Prevention Systems (IDPS): Detect and prevent malicious activities at the network boundary.
- Demilitarized Zone (DMZ): Segregates public-facing services from the internal network.
- Virtual Private Networks (VPNs): Secure remote access to the network.
2. Network Security
- Network Segmentation: Divides the network into segments to limit the spread of attacks.
- Network Access Control (NAC): Ensures that only authorized devices and users can access the network.
- Secure Routing and Switching: Protects data integrity and confidentiality in transit.
- DDoS Protection: Mitigates the impact of Distributed Denial of Service attacks.
3. Endpoint Security
- Antivirus and Anti-Malware: Detects and removes malicious software.
- Endpoint Detection and Response (EDR): Provides advanced monitoring and response capabilities for endpoints.
- Patch Management: Keeps software up to date to protect against known vulnerabilities.
- Device Encryption: Protects data on endpoints, such as laptops and mobile devices.
4. Application Security
- Secure Development Practices: Incorporates security into the software development lifecycle (SDLC).
- Web Application Firewalls (WAFs): Protects web applications by filtering and monitoring HTTP/HTTPS traffic.
- Code Reviews and Security Testing: Identifies and fixes vulnerabilities in application code.
- Application Whitelisting: Ensures only approved applications can run on systems.
5. User Security
- Identity and Access Management (IAM): Manages user identities and controls access to resources.
- Multi-Factor Authentication (MFA): Adds an additional layer of verification for user authentication.
- User Training and Awareness: Educates users about security policies, procedures, and best practices.
- Phishing Simulations: Trains users to recognize and respond to phishing attempts.
6. Data Security
- Data Encryption: Protects data at rest and in transit from unauthorized access.
- Data Loss Prevention (DLP): Monitors, detects, and prevents unauthorized data transfers.
- Access Controls: Ensures only authorized users have access to sensitive data.
- Data Classification and Labeling: Identifies and categorizes data based on its sensitivity.
Conclusion
Defense in Depth is an essential strategy that layers multiple security measures to protect an organization’s assets and data. By implementing perimeter security, network security, endpoint security, application security, user security, and data security, organizations can create a robust defense against a wide range of threats. Each layer addresses different aspects of security, ensuring that if one layer is compromised, others continue to provide protection. This multi-faceted approach enhances the overall security posture and resilience of the organization.