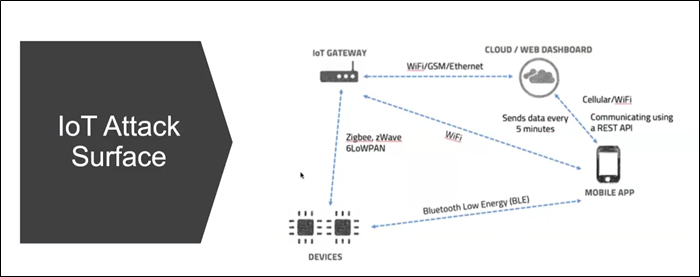
Elements of IOT Attack Surface
1. Device: The “Device” component is central to any IoT architecture. In this context, “device” refers to any hardware involved in the system.
For instance, in many smart home appliances, the term “device” typically includes both the “gateway” and the “operating device.” The gateway functions as the central hub connecting other devices, while the “operating device” performs the intended actions or monitoring tasks using sensors, depending on its purpose.
Vulnerabilities in the “device” category are akin to those found in embedded systems. Examples include issues like unauthorized access through serial ports and the ability to extract firmware from flash memory. We will delve deeper into these vulnerabilities in the detailed exploration of the device section in upcoming posts.
2. Bluetooth Low Energy (BLE): In the context of firmware, BLE refers to the implementation of the Bluetooth Low Energy protocol within the firmware of a device. BLE is a wireless communication protocol designed for low power consumption and is commonly used in various devices for short-range communication.
Usage of BLE:
Communication: BLE enables devices to communicate with other Bluetooth-enabled devices efficiently. Firmware must handle BLE communication protocols, including establishing connections, managing data transfer, and maintaining power efficiency.
Low Power Operation: BLE is designed to operate with minimal power consumption, which is crucial for battery-operated devices. Firmware is responsible for managing BLE power states and optimizing power usage.
Device Pairing and Bonding: Firmware handles the pairing and bonding processes, which involve establishing and maintaining secure connections between devices.
Profiles and Services: BLE defines various profiles and services that firmware must support. These profiles dictate how data is exchanged between devices. For example, a fitness tracker might use BLE profiles to communicate heart rate data to a smartphone app.
Firmware Updates: BLE can be used to update firmware wirelessly. The firmware may include mechanisms for receiving, verifying, and applying firmware updates over BLE.
Security: BLE firmware must implement security features like encryption and authentication to protect data exchanged between devices.
3. Mobile Application: It’s the device from where you can control the IOT devices.
4. Cloud Web Dashboard: Web Application dashboard to control and modify the setting of iot device.
5. Radio Communication: The radio communication is a critical aspect of any IoT device. By Radio communication, we simply mean any communication is happening between device-device or app-device.
The various communication protocols which are usually used in an IoT architecture are WiFi, BLE, Zigbee, ZWave, 6LoWPAN and Cellular to name a few.