A risk matrix in cybersecurity is a tool used to evaluate and prioritize risks based on their likelihood and potential impact. It provides a visual representation of risks, helping organizations identify which threats require immediate attention and resources. The matrix typically consists of a grid where one axis represents the likelihood of a risk occurring, and the other axis represents the impact or severity of the risk. Each cell within the grid corresponds to a specific combination of likelihood and impact, allowing for a clear and concise assessment of risks.
Components of a Risk Matrix
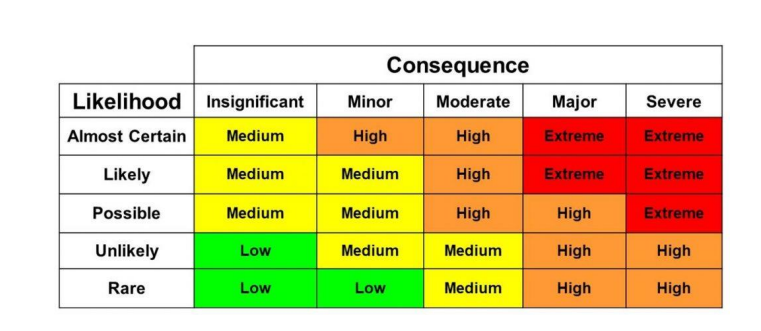
- Likelihood: The probability that a particular risk will occur. This is often categorized into levels such as:
- Rare
- Unlikely
- Possible
- Likely
- Almost Certain
- Impact: The potential consequences or severity of the risk if it were to occur. Impact levels are typically categorized as:
- Insignificant
- Minor
- Moderate
- Major
- Catastrophic
- Risk Score: Each combination of likelihood and impact is assigned a risk score, often represented by colors or numerical values, to indicate the severity of the risk. For example:
- Low Risk (Green): Acceptable risk, requiring minimal or no action.
- Medium Risk (Yellow): Risk that should be monitored and may require mitigation.
- High Risk (Red): Critical risk that requires immediate action and mitigation.
Creating a Risk Matrix
To create a risk matrix, follow these steps:
- Identify Risks: List all potential cybersecurity risks that the organization may face. This can include threats like malware, phishing attacks, insider threats, data breaches, and more.
- Assess Likelihood: Evaluate the likelihood of each risk occurring, based on historical data, threat intelligence, and expert judgment.
- Assess Impact: Determine the potential impact of each risk on the organization, considering factors such as financial loss, reputational damage, legal implications, and operational disruption.
- Map Risks: Plot each risk on the matrix based on its likelihood and impact. This involves placing risks in the appropriate cells of the grid.
- Analyze and Prioritize: Use the visual representation to analyze the risks. Prioritize risks based on their position in the matrix, with high-likelihood and high-impact risks receiving the most attention.
Conclusion
A risk matrix is a valuable tool in cybersecurity for systematically evaluating and prioritizing risks based on their likelihood and impact. By visualizing risks in a structured format, organizations can better understand their risk landscape and allocate resources effectively to mitigate the most significant threats. This proactive approach helps enhance the overall security posture and resilience of the organization.
Discover more from Upcoming Hackers
Subscribe to get the latest posts sent to your email.